Bi-monthly news update from IsDB-BISEW IT Scholarship Programme (January 2025)
Mar 04, 2025 / IT Scholarship ProgrammeEmpower

Welcome to the January 2025 issue of Empower, the periodic newsletter of the IsDB-BISEW IT Scholarship Programme. This edition includes the following topics of note:
-
A Guide to Cyber Security for Beginners
-
Mily’s Story – The Transformative Impact of the IsDB-BISEW IT Scholarship Programme
A Guide to Cyber Security for Beginners
(Adapted from simplilearn.com)

Cybersecurity is a popular topic, but do you know why it is essential? We are living in a digital era where data is everything. We must understand that private information is much more vulnerable than ever before. Data breaches and identity theft cases often affect millions of consumers. Two years ago, WannaCry ransomware encrypted millions of computers. All companies and institutions are fighting to protect their data against hackers and cybercriminals, and you can also play a role in it. Cybersecurity is involved not only in organisations but also in personal computers, mobile phones, and tablets.
What is Cybersecurity?
Before we begin this article, let's first understand what cybersecurity is and its significance. Cybersecurity is the technology and process designed to protect networks and devices from attacks, damage, or unauthorised access.
Cybersecurity is essential for a country’s military, hospitals, large corporations, small businesses, and other organisations and individuals since data is now the cornerstone of any organisation. If that data is exploited, there are many risks. Now that we have understood cybersecurity, let’s see what the CIA triad is and how it relates to cybersecurity.
CIA Triad
The security of any organisation starts with three principles: Confidentiality, Integrity, and Availability. This article will teach us about the CIA Triad, the industry standard for computer security since the first mainframes.
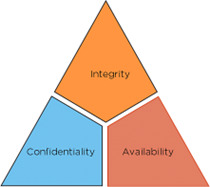
- Confidentiality: The principles of confidentiality assert that only authorised parties can access sensitive information and functions. Example: military secrets.
- Integrity: The principles assert that only authorised people and means can alter, add, or remove sensitive information and functions. Example: a user entering incorrect data into the database.
- Availability: The availability principles assert that systems, functions, and data must be available on demand according to agreed-upon parameters based on service levels.
Let’s look at the areas and specialties in cybersecurity to understand the space better.
Specialties in Cybersecurity
To pursue a career in cybersecurity, it is essential to know about the areas of specialisation in it, and this cybersecurity article will help you do just that. There are nine specialities:
- Access control systems and methodology: This protects critical system resources from unauthorised modification.
- Telecommunications and network security: This focuses on communications, protocols, and network services, as well as the potential vulnerabilities associated with each.
- Security management practices: This area effectively deals with catastrophic system failures, natural disasters, and other service interruptions.
- Security architecture and models: This focuses mostly on having security policies and procedures in place. This particular security domain involves policy planning for just about every type of security issue.
- Law, investigation, and ethics: This handles the legal issues associated with computer security.
- Application and system development security: This person covers database security models and implements multilevel security for in-house applications.
- Cryptography: Designed to help you understand how and when to use encryption.
- Computer operations security: This covers everything that happens while your computers are running.
- Physical security: This addresses questions about physical access to your servers and workstations.
Basic Terminologies
- Network
A network is a connection between two or more computers that communicate. For example:

- Internet
Internet connects a computer to any other computer anywhere in the world via dedicated routers and servers.
- Internet Protocols
Data that is transferred or received cannot follow any path. A set of rules is followed to control the flow of the Internet. These rules are called the Internet protocol.
- IP Address
An Internet Protocol address (IP address) is assigned to all devices that connect to a computer network and use the Internet Protocol for communication. An IP address looks like this: 168.192.10.3
- MAC Address
Every device has a unique identification number that connects to the internet. Traditional MAC addresses are 12-digit hexadecimal numbers. MAC address looks like this: D8-FC-93-C5-A5-EO.
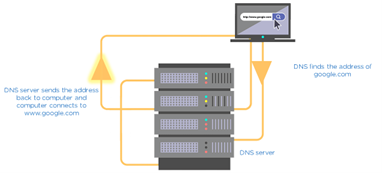
- Domain Name Server (DNS)
Consider DNS as the phonebook of the internet. All the IP addresses and the names of the links are saved in it. For example, you want to go to google.com. You type this on your web application. Then, this name goes to the DNS server, and the DNS server finds the IP address of google.com. Then, the DNS server returns it to your computer with the IP address.
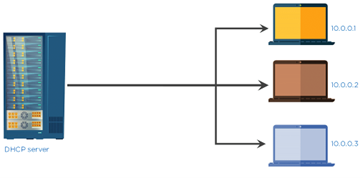
- DHCP
The dynamic host configuration protocol assigns an IP address to any device that wants to connect to the Internet.
- Router
This device routes the data that comes to it and then sends it to the destination to ensure that it is on the appropriate path.
- Bots
Bots are computer programs that control your computer without your knowledge. They automatically send emails, retrieve web pages, and change computer settings.
Common Types of Attacks
Before we get into the types of attacks, we should know why these attacks happen, and this article will help you learn A-Z of both. Every attack has a motive; the main reason for attacks is money. Hackers penetrate the system and then demand ransom from the victims. There are other reasons, such as a financial loss to the target, a state’s failure to achieve its military objective, damage to its reputation, or political manoeuvring.
There are mainly five types of attacks:
- Distributed denial of service (DDoS)
- Man in the middle
- Email attacks
- Password attacks
- Malware attack
In the next section of this article, let’s look at all the attacks in detail:
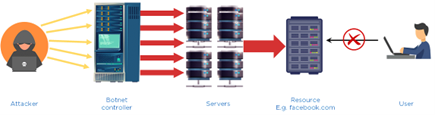
- Distributed Denial of Service
It is an attack used to restrict a user from accessing resources by flooding the traffic that is used to access resources. A botnet controller controls all the bots under it. The attacker sends a command to the botnet controller that tells all bots to attack a server so that the server will be flooded. When a user wants to access a website, he will not be able to, as the traffic on the website will be at full capacity.
- Man in the Middle
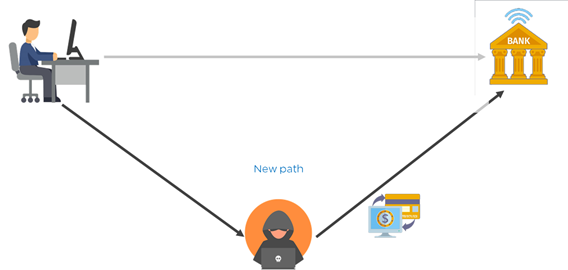
Let’s look at an example to understand this better. Suppose you want to do an online transaction, and you connect to your bank and make the payment.

Now, while you are completing the transaction, you have to enter your credit card details and PIN. The attacker can spoof you and monitor your transaction. As soon as you enter your details, he will see them.
- Password Attack
We use this technique to crack or find a password. There are five types of password attacks:
- Dictionary attack: In this method, we handle every possible password through the dictionary.
- Brute force: This trial-and-error method decodes the password or data. This attack takes the most time.
- Keylogger: As the name suggests, a keylogger records all keystrokes on a keyboard. Most hackers use keyloggers to get passwords and account details.
- Shoulder surfing: The attackers observe the user’s keyboard by looking over the user’s shoulder.
- Rainbow table: Rainbow tables contain precomputed hash values. Attackers use these tables to find a user's password.
- Email Attacks
First, let’s see how an email works. Suppose John is sending an email to Jack. The email first goes to the email server. Then, it goes to the DNS server to find the destination's IP address. From the source email server, the email goes to the destination server. From there, the email is sent to the IP address on which Jack is working. This is illustrated in the picture below.
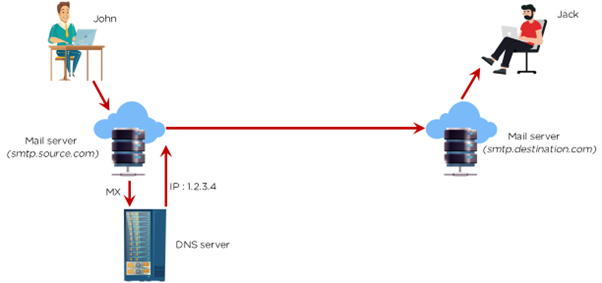
There are three types of email attacks.
- Phishing: The attacker sends bait, often in the form of an email. It encourages people to share their details. For example, you receive an email like this:
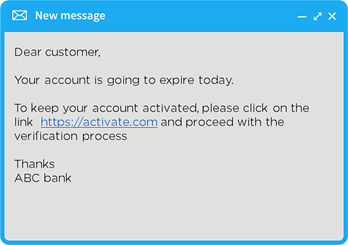
If someone is a customer of ABC Bank, he would probably open the link and give the details. However, these emails are always phishing; banks do not send emails like this.
- Spoofing: The attacker pretends to be another person or organization and sends you an email stating it is legitimate. For example:
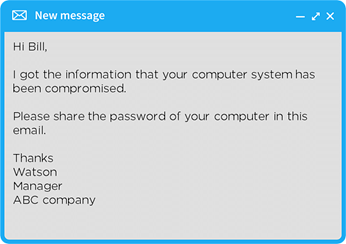
After seeing this email, you might share the password to your computer. Always ask the person from whom you received the email one more time to confirm that he is the right person.
- Email attachments: You can send files through emails. These files may be images, documents, audio, or videos. Attackers send you an email, and you are encouraged to open the attached file. For example:
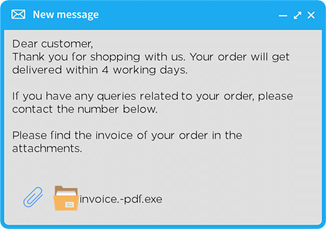
Download these attachments only if you know it is a legitimate email.
- Malware Attack
- Malware: This is a malicious program or software that disrupts or damages the computer. There are three types of malware.
- Virus: A computer virus is a malicious code that replicates by copying itself to another program or document and changes how a computer works. The virus requires someone to knowingly or unknowingly spread the infection without the knowledge or permission of a user or system administrator. An example of a virus is the Melissa virus.
- Worms: These are standalone programs that run independently and infect systems. For example, W32.Alcra.F is a worm that propagates through network share devices.
Functions of Malware
- Overwhelming system resources: Malware, especially worms, can spread around and overwhelm a system or network. Some malware creates so many folders that no memory is left and slows a computer down.
- Creating a backdoor: Let’s look at an example: Microsoft sends updates every Sunday on all Windows platforms. How do these updates reach to your Windows OS? They create backdoors from where they can send updates. Similarly, hackers create backdoors from where they can continuously send viruses after getting into a system.
- Disabling security functions: Some malware can disable antivirus software and security updates. This malware tends to last longer because there is no security to stop it, and it tends to keep the system vulnerable to other malware.
- Creating botnets: Hackers create botnets by purely coding. A botmaster controls botnets, which are usually used to crash websites. The botmaster tells all botnets to flood the website by accessing it at the same time.
Sources of Malware
- Removable media: Removable media, such as pen drives, CDs, DVDs, and flash drives, may be used to send viruses to your system.
- Documents and executable files: Viruses can be hidden in document files with the .exe extension. As soon as you open them, the virus activates.
- Internet downloads: Download files only from trusted websites. If you download from untrusted websites, there is a chance that those files will contain viruses, and as soon as you open them, the hacker might get access to your system.
- Network connections: Be sure that your service provider is genuine. If the network is unsecured, then anyone can access it.
- Email attachments: Never open email attachments unless the sender can be trusted. These files may contain viruses that can create backdoors.
- Malicious advertisements: Never click on ads that you don’t trust. They are created to get you to click on them, and hackers will receive details about you.
Job Roles
The kind of job you do is something you wish to consider before you step foot in any field. In this section of the article, we will learn about the top roles in the cybersecurity field:
- Chief Information Security Officer: Manages the organisation's IT security division.
- Forensic Computer Analyst: Looks for evidence after the breach or attack on an organisation.
- Information Security Analyst: Protects the computer systems and networks of an organisation.
- Penetration Tester: Penetration testers are highly skilled security specialists who spend their days attempting to breach computer and network security systems.
- IT Security Engineer: Plan to carry security measures to monitor and protect data and systems from hackers and cyber-attacks.
- Security Architect: Maintain the network security of an organisation.
- Security Systems Administrator: Their responsibilities include installing, administering, maintaining, and troubleshooting computer, network, and data security systems.
- IT Security Consultant: Protect the organisation’s sensitive data.
Mily’s Story – The Transformative Impact of the IsDB-BISEW IT Scholarship Programme
Name: Tazrimin Rahman Mily, Back-end Engineer
Course: Enterprise Systems Analysis & Design with C#.NET
Round: 41

Tazrimin Rahman Mily, a talented software engineer from Bangladesh, is currently employed full-time as a remote back-end developer for a Canadian company. Her employer highly values her expertise and technical proficiency, entrusting her with a critical role within the organisation.
What makes Mily’s journey remarkable is that she does not hold a degree in Computer Science. Instead, her academic background is in Physics, with both her bachelor’s and master’s degrees in the subject. How, then, did she transition into a thriving career in software engineering? The answer lies in her determination and the pivotal role played by the IsDB-BISEW IT Scholarship Programme.
Mily grew up in Netrokona, where she completed her Secondary School Certificate (SSC) in 2008 and Higher Secondary Certificate (HSC) in 2010. Tragedy struck when she lost her father just three months before her HSC examinations. Despite the emotional turmoil, she persevered and successfully passed her exams.
With a clear vision for her future, Mily chose to study Physics at Mymensingh Anondo Mohon College. Aware that this decision meant living away from her family, she prioritised academic excellence over comfort. With the unwavering support of her younger brothers, she completed her undergraduate degree in 2017. Building on this achievement, she moved to Dhaka and earned her master’s degree in Physics from Lalmatia Mahila College in 2019.
During her master’s studies, Mily observed her peers preparing for the BCS civil service exams. However, a government career did not align with her aspirations. Instead, she was drawn to the world of technology and became fascinated by IT. Driven by curiosity, she began learning basic web technologies such as HTML and CSS through online tutorials on YouTube. A friend introduced her to the IsDB-BISEW IT Scholarship Programme, which provided fully funded training in specialised IT fields. Enthusiastic about the opportunity, Mily applied and was selected in Round-41 for a programming course.
Initially, the intensive training seemed challenging, as programming was entirely new to her. However, the well-structured curriculum and the guidance of expert instructors enabled her to grasp complex concepts. With perseverance and dedication, she successfully passed all her exams and completed the year-long training programme.
Upon completing her course, the Placement Cell of the IT Scholarship Programme secured her first job as a programmer at Opus Technology Ltd, a reputed software firm in Dhaka. Reflecting on her transition into the industry, Mily acknowledges the effectiveness of the training: “The IsDB-BISEW training was so comprehensive and industry-oriented that I found working as a programmer straightforward and uncomplicated.”
Today, Mily is excelling as a back-end software engineer for a Canadian company specialising in property management software. Earning an internationally competitive salary, she credits the IsDB-BISEW IT Scholarship Programme for her professional success. “The IT Scholarship Programme helped me secure a professional career at an international level, something I could never have achieved otherwise.”



